Okta
This guide walks you through the process of setting up Single Sign-On (SSO) with Okta for the platform. By following these steps, you'll enable seamless authentication for your users through Okta.
Create A New App In Okta
Start by creating a new Okta App for the platform.

Okta - Create a new App in Okta Select "Web" App and ensure OpenID Connect is the single sign-on method.
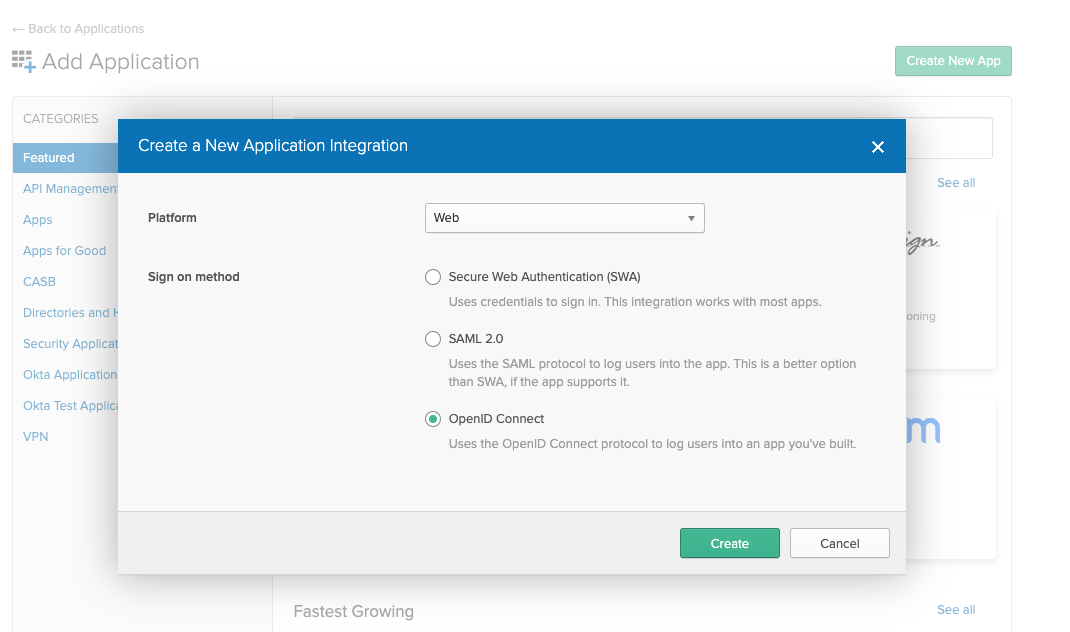
Okta - Web App with OpenID Connect as single sign on method
On the next screen, configure the login redirect URIs to include your platform instance domain:
Configure login redirect URI# Replace ${my-loft-domain.com} with your platform domain
https://${my-loft-domain.com}/auth/oidc/callback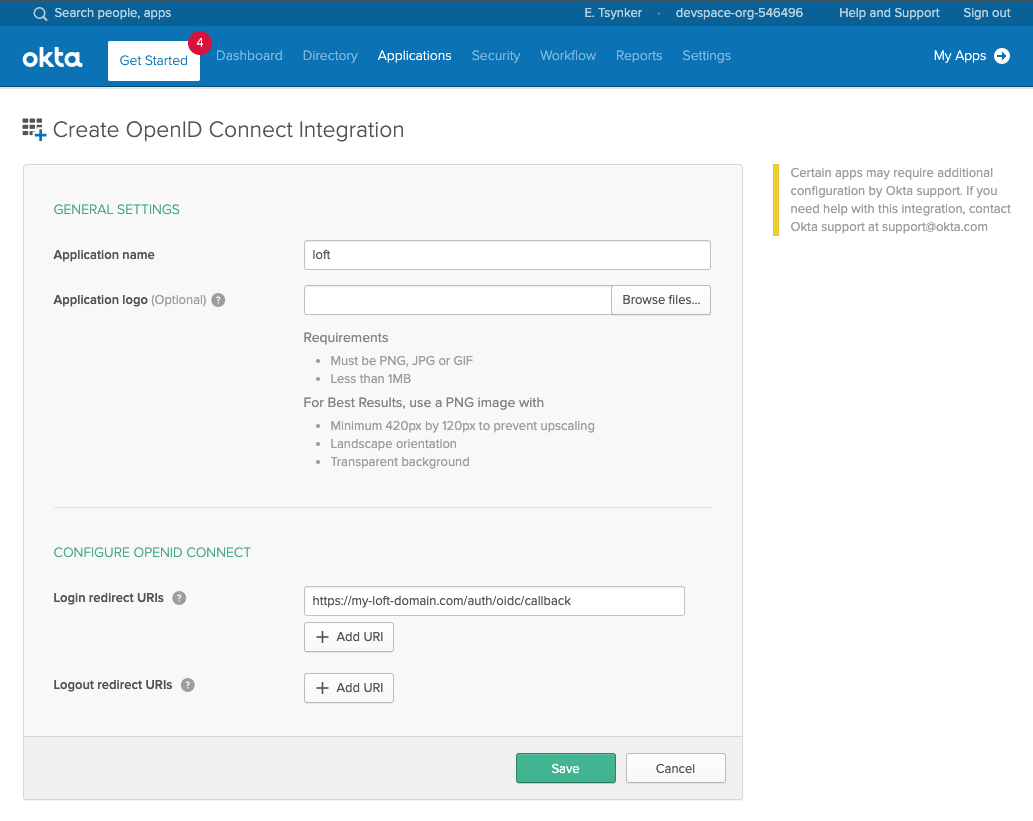
Okta - The App settings for the platform Enable Refresh Tokens
After creating the Okta app for the platform, enable "Refresh Token" under "Allowed grant types". This step is crucial as it allows users to maintain their session without frequent re-logins.
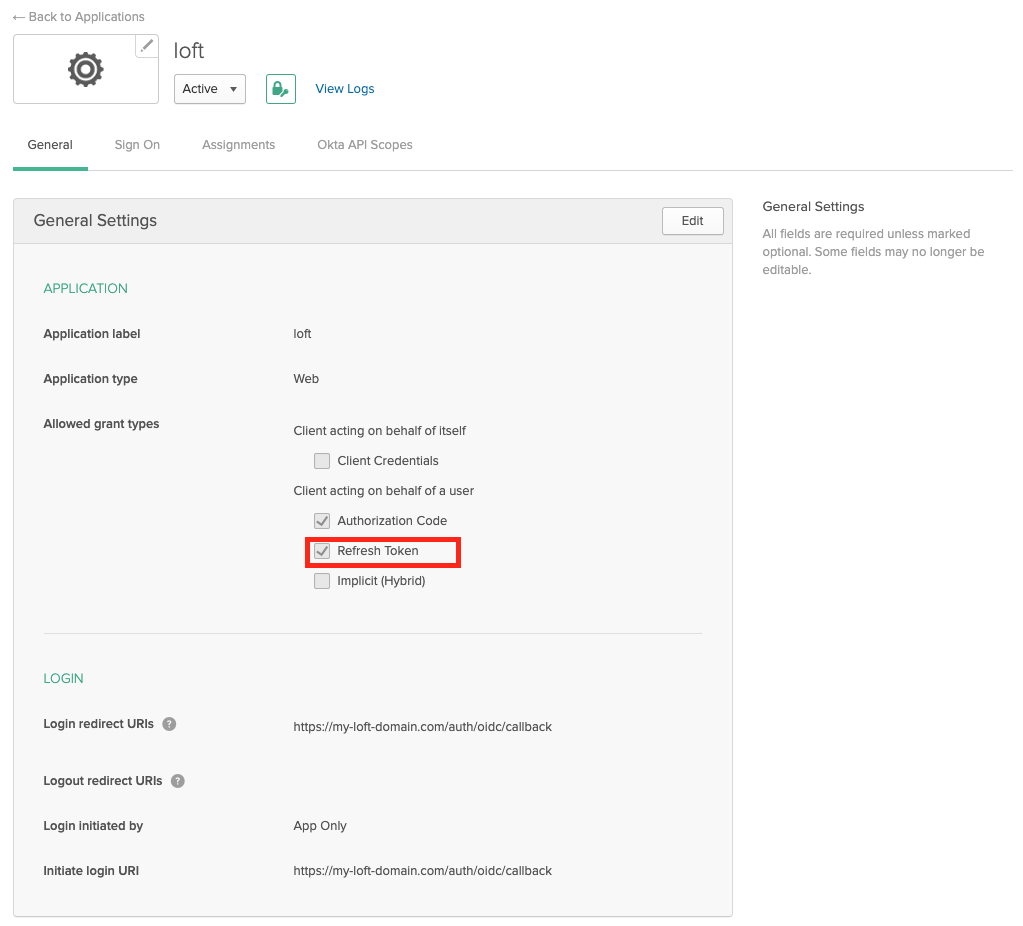
Okta - App Settings: Enable Refresh Tokens Enable Group Claims
If you want to propagate the users groups to the platform, then make sure the Group Filters in Okta are set accordingly. If you want to propagate all groups, add a RegEx filter with '.*'
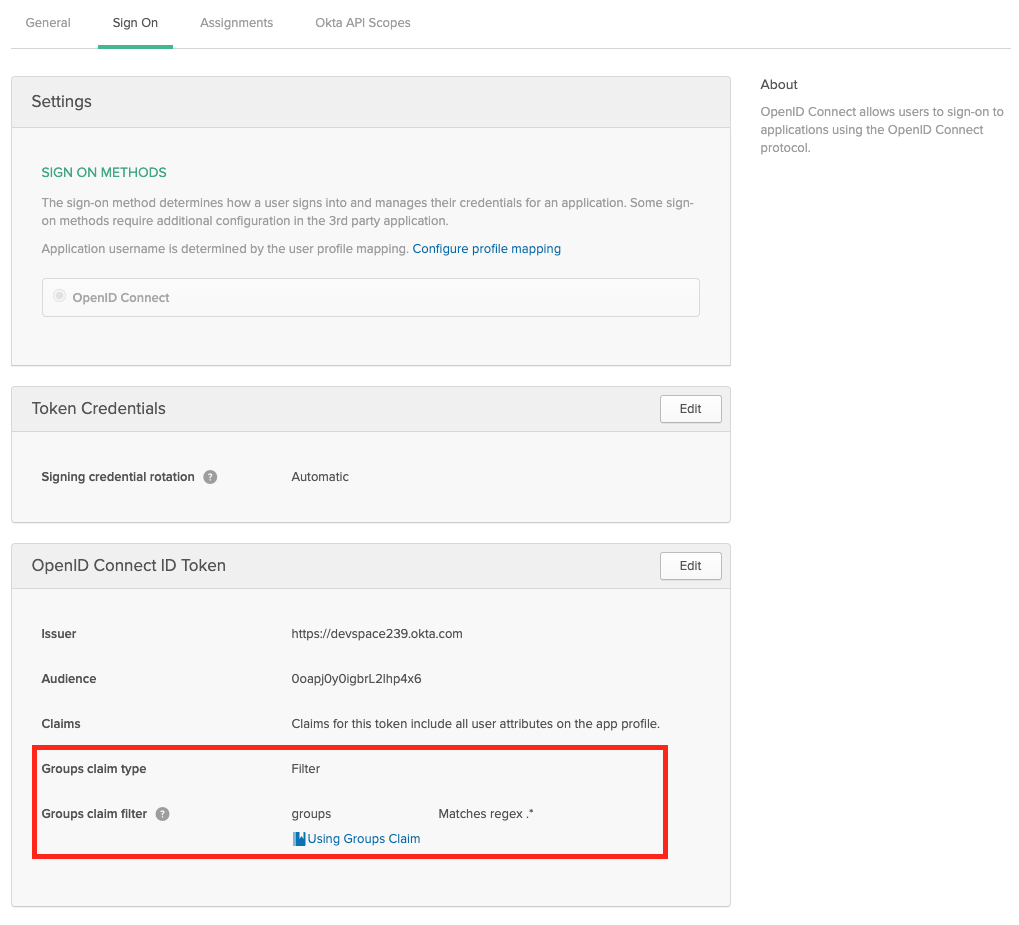
Okta - Propagate User Groups To the platform Configure platform to use Okta
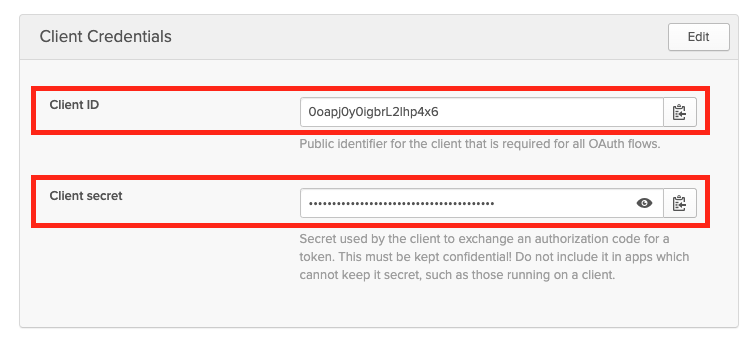
Okta - Client ID and Secret For App Navigate to
Admin > Configin the platform and enter the following configuration:Configure the platform for Okta integrationauth:
oidc:
issuerUrl: "https://${MY-OKTA-SUBDOMAIN}.okta.com"
clientId: CLIENT_ID
clientSecret: CLIENT_SECRET
groupsClaim: groups
# This is needed because Okta uses thin id tokens
# that do not contain the groups directly
getUserInfo: trueThe
groupsClaimfield specifies where to find group information in the token, andgetUserInfois set totrueto retrieve additional user information from Okta.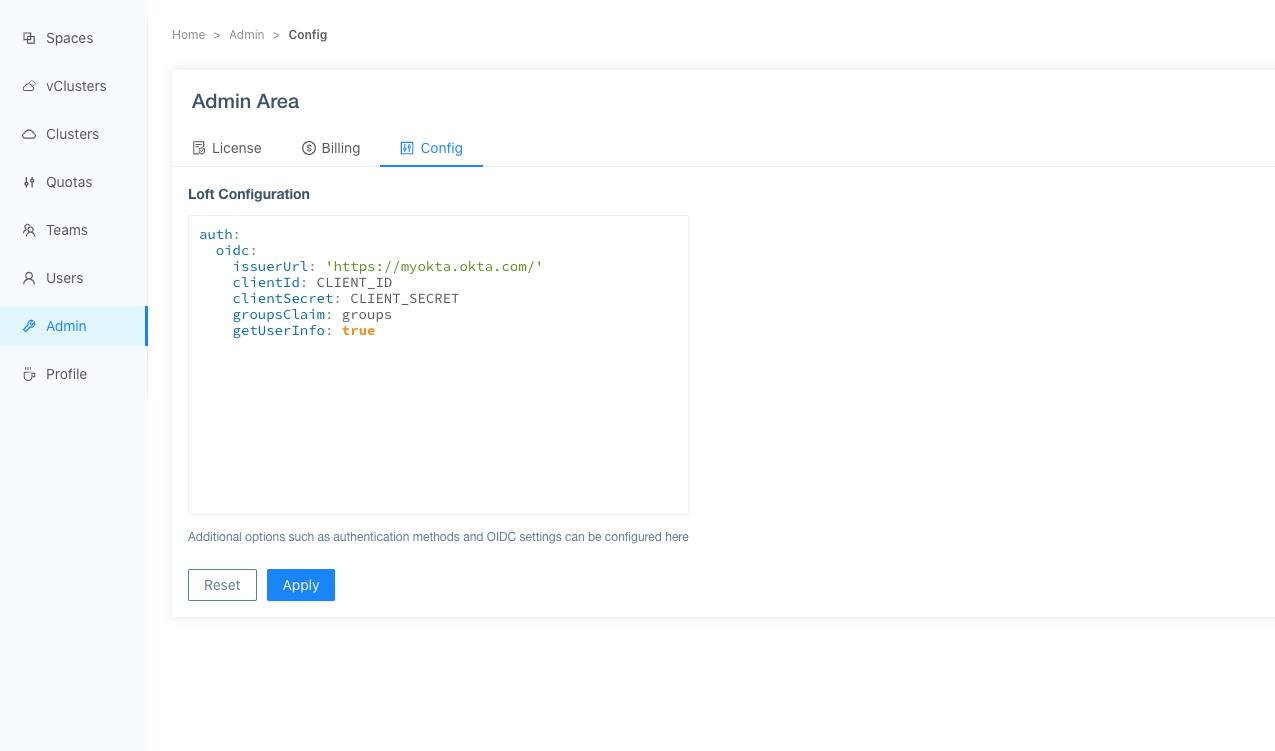
Configure the platform To Use Okta Add Users via Okta Assignments
Assign the appropriate Users and Groups to access the platform in Okta.
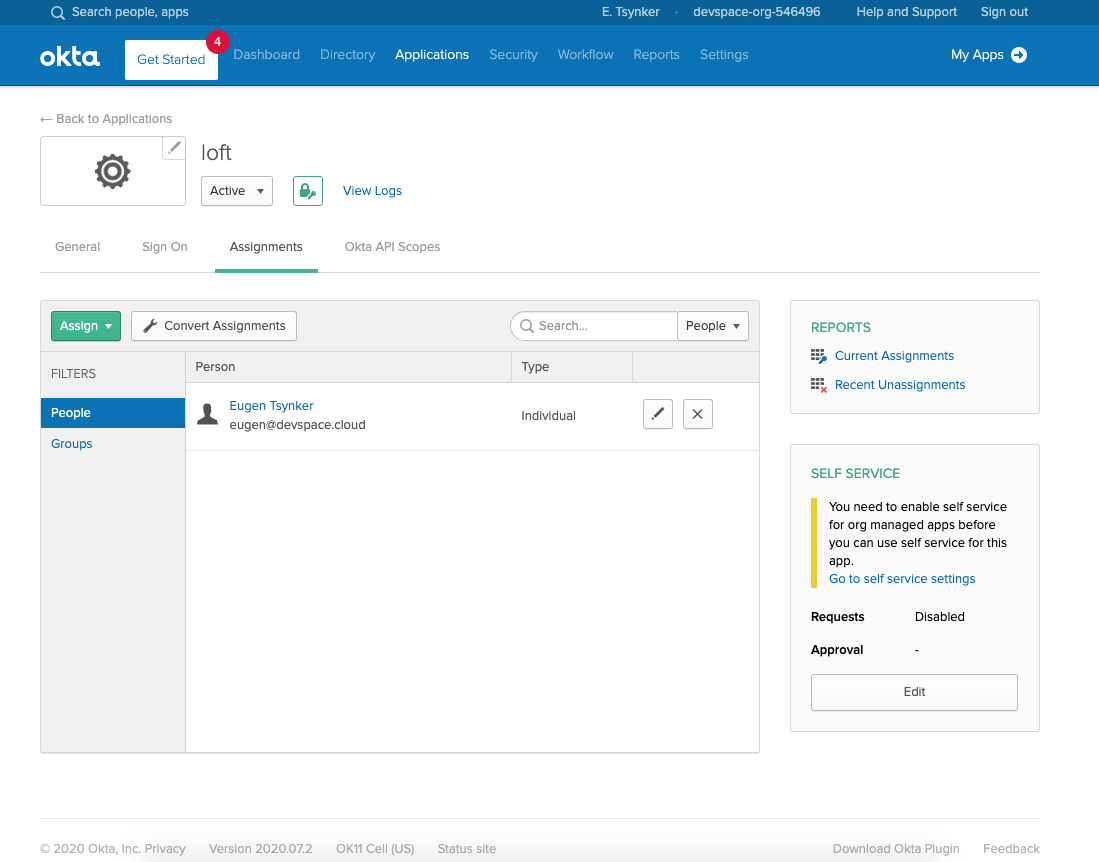
Okta - Assign Users & Groups To the platform Once users or their groups are assigned to the platform, they can log in via Okta:
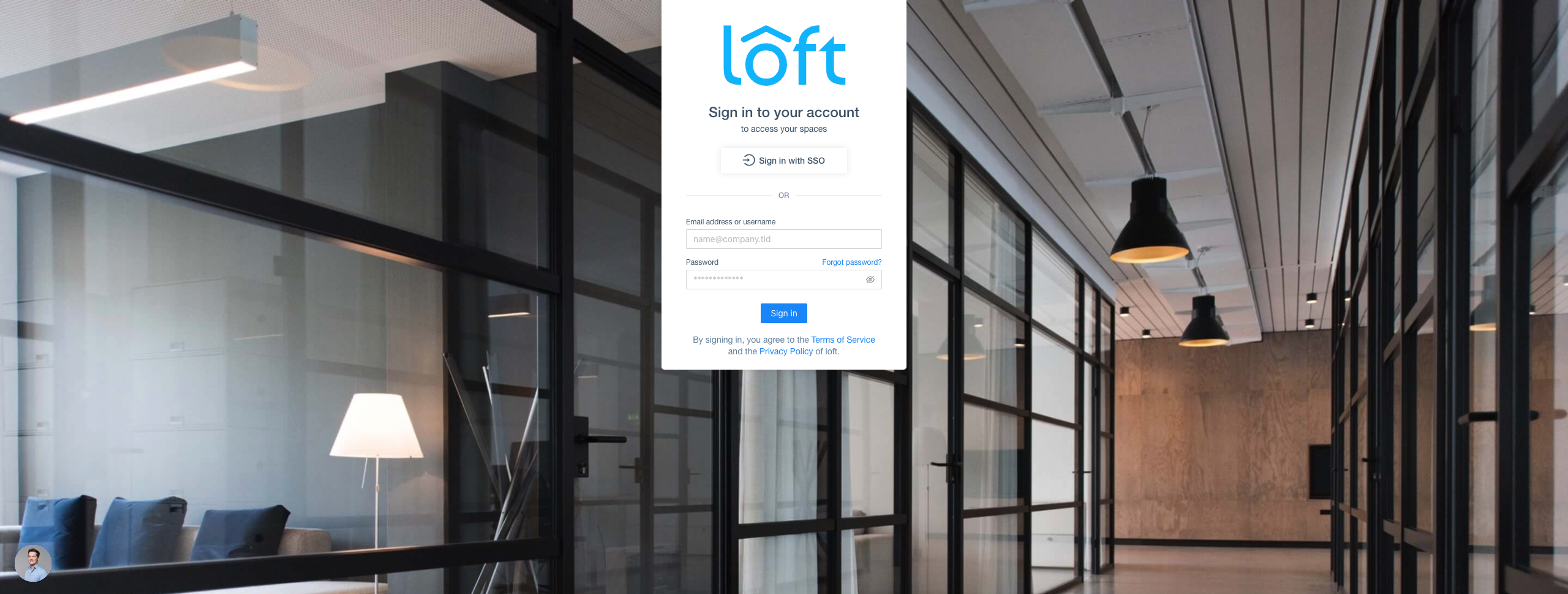
The platform - SSO via Okta Disable Username + Password Authentication (optional)
To turn off password-based authentication, navigate to
Admin > Configadd these two lines to your config:Disable password-based authenticationauth:
oidc: ... # This is your SSO configuration (make sure this is working!)
password:
disabled: true # Disable password-based authentication